DCS is recognised as a key enabler for NATO to evolve towards digital transformation exploiting new technologies and processes that treats data as a strategic resource to help inform timely decision making at all political and military levels across multiple domains of operations.
NATO vision for DCS is to deliver shareable, timely and reliable information: protected at source; and, controlled for life.
NATO strategy for implementing DCS is evolutionary defined by three Maturity Levels (MLs), whereby each ML facilitates interoperability and builds ontop of each other to reach the defined end-state.
DCS ML 1: Basic Labelling (DCS-1) – Facilitated by the NATO standards (STANAG 4774, STANAG 5636 and STANAG 4778) to provide consistent, reliable and trustworthy labelling with metadata associated for use with all common types of file formats and core services. Use of the XMLSPIF is fundamental for ensuring confidentiality metadata (STANAG 4774 confidentiality label and confidentiality clearance) is consistently applied and consistently displayed based upon the governing security policy that is being enforced.
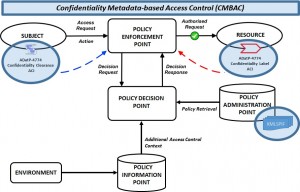
DCS ML 2: Enhanced Labelling (DCS-2) – Facilitated by the emerging NATO standard (STANAG 5663) to provide federated identity and access management (FIAM) and facilitate attribute-based access control (ABAC). The “Holy Trinity” (not George Best, Dennis Law and Sir Bobby Charlton) of STANAG 4774 confidentiality label, STANAG 4774 confidentiality clearance and XMLSPIF are used to provide Confidentiality Metadata-based Access Control (CMBAC; pronounced as “Come Back“), fundamental for facilitating ABAC. XMLSPIF specifies the rules for how CMBAC is enforced based upon comparing the confidentiality metadata value domains provided in a STANAG 4774 confidentiality label (associated with a resource) against a STANAG 4774 confidentiality clearance (associated with a Subject i.e. a user, application, device or service). Implementation of CMBAC (as illustrated below), through the ratification of ADatP-5663: Federated Identity, Credentials and Access Management, is recognised as a core capability for evolving NATO DCS vision and strategy towards achieving DCS-2.
DCS ML 3: Cryptographic Protection (DCS-3) – NATO are currently developing an interoperable, standardised and federated approach for achieving DCS-3.
Recent Comments